Stay in the know
We’ll send you the latest insights and briefings tailored to your needs
This comes down to building internal ‘muscle memory’ and ensuring that businesses are prepared to navigate difficult judgment calls with poise in the heat of an incident response. “As a community, we’ve crossed the Rubicon in terms of recognising that even companies that have heavily invested in cyber protections may well have an incident,” says Carolyn Pugsley, a senior partner in Herbert Smith Freehills’ corporate governance team. “Now is the time to focus on what a good response looks like from a reputational perspective.”
Accountability, transparency and empathy are guiding principles in protecting reputation and re-establishing trust in the aftermath of a crisis. Companies need to balance obligations to agencies and regulators, alongside communicating with customers and the public. Minimising potential legal losses should be a factor, but not the primary lens through which decisions are considered. Being seen as transparent and empathetic to stakeholders affected by a data breach may remain the right path, even if it impacts the organisation’s legal rights and entitlements, including its ability to claim against a third-party.

In a crisis, organisations are pushing uphill to re-establish the trust that has been eroded by the breach. Reputation is critically linked to organisational survival. In a crisis response, stakeholders are given a clear view of the company's narrative, and its alignment or misalignment, with actions. Values-based communications are inextricably linked with a company’s public license to operate, and this can be more critical in a crisis than simply minimising your legal exposure.
Legal teams have an important role to play in framing disclosures and disseminating accurate information. “Jumping out too fast, to push out information that isn’t reliable and from which the business may need to backtrack only feeds a perception that you’re not on top of the incident and not credible,” Pugsley says.
Ransom payments fall out of vogueWe expect many Australian organisations will soon be required to disclose any extortion payments made in the context of a cyber incident. However, our survey data suggests a sustained trend away from paying ransom. |
|
|
Consistent with last year’s findings, a significant minority of those surveyed are aware of ransoms being paid in the context of cyber incidents. This is consistent with our experience. “The starting point in almost all cases is that organisations won’t pay a ransom. Whereas if you rewind 12 or 18 months, that issue was up for grabs,” Pugsley says. This trend is generally consistent with recent findings from the global incident response firm, Coveware, whose Q2 2024 report depicts a general decline in the proportion of clients choosing to pay a ransom since Q1 2023.2 Coveware reported that: “In Q1 2024, the proportion of victims that chose to pay touched a new record low of 28%.”3 Our survey reveals that nearly 40% of boards have not decided (in advance of any cyber-attacks) whether they would be open to paying a ransom. However, it is unclear whether this cohort has the decision-making tools and legal advice needed to help them navigate this complex topic in the heat of an incident, or whether these boards intend to adopt a reactive approach. What we do know is that ransom discussions are complex. Paying a ransom can itself be an offence, under instrument of crime or terrorism financing law, for example, or if the organisation or individual receiving the funds is sanctioned (a strict liability offence). |
The Australian Government established a thematic autonomous sanctions regime in 2021. This was first used on two individuals in 2024. Newton says, “the use of thematic autonomous sanctions adds a new component to the risk framework relevant to paying a ransom demand, as there is a heightened risk that a ransom payment may be directly or indirectly going to one of these individuals”. In our view, these concerns must be balanced against the operational impact of an attack, including on health and safety, and the overall best interests of the company. Indeed, paying a ransom demand may be the right path for an affected company. New mandatory disclosure laws in Australia will hopefully shine a light on the scale of the problem, and this data can be effectively used by government to deliver targeted support for vulnerable sectors, particularly small-to-medium sized businesses. |
Carolyn Pugsley
Partner

The vulnerability of organisations to third parties is particularly topical in light of the CrowdStrike global outage in July 2024. “While not a cyber incident, CrowdStrike has shown how interdependent we all are,” says Peter Jones, a corporate partner who specialises in complex technology and information transactions. “In a different context that could have been a cyber-driven impact. For example, the effect could have been materially worse had it been a malicious third-party that co-opted the platform."
Despite ranking as a key concern, addressing third-party risk was not prioritised by surveyed organisations in the past 12 months. There are lots of possible explanations but confusion over ownership of this risk within the business is likely to blame. Possibly, the CrowdStrike outage may be the sobering wake-up call that refocuses attention.
Mitigation of third party-related software risk is now a cornerstone of effective cyber risk management. “Given the interconnectedness of commercial relationships, it’s not just the entity with which you directly deal, it’s the entity beyond that and the one beyond that and so on,” Jones says. Third-party risk extends to understanding how data is shared and managed by external parties. Many organisations provide highly sensitive commercial content to third and fourth-party service providers while conducting business. “These vendors are often the weakest link in the data management chain, and security controls must be implemented to manage these relationships and risks,” Jones says. It is also necessary that relevant insurance programs are set up such that the loss caused by a third-party is adequately covered.
These weak links have not escaped government and regulatory attention. In the 2023–2030 Cyber Strategy, the government acknowledged the issue with insufficiently secure products and services being made available to businesses (and consumers), describing it as a 'market failure' that it is seeking to address. In July 2025, we expect Prudential Standard CPS 230 to take effect, which would require APRA-regulated organisations to effectively manage operational risks arising from service providers.

There are many ways that a company can build a more robust supply chain. These include thorough due diligence, comprehensive onboarding and enforceable standards in vendor contracts. Contract privity between different parties in a supply chain can make it hard to flow through legal obligations. However, as ASIC Chair Joseph Longo said in 2023,4 “[it]’s not enough to sign a contract with a third-party supplier – you need to take an active approach to managing supply chain and vendor risk. Setting it and forgetting it, does not, cannot, and will not work.”
It is possible for a company to be subjected to customer claims in connection with the impacts on affected customers of poor supply chain management. Additionally, relevant regulators could bring an action against an organisation that had not discharged its obligation to manage third-party risk, especially given the role of directors to provide supervision of the corporate entity. “Good risk management would look at third-party risk issues. It comes back to organisations making general decisions about their risk exposure and what they can do to mitigate this,” Jones says.
Jason Betts
Partner and Global Co-Head of Class Actions




The law with respect to class actions involving cyber incidents remains untested as no such case has proceeded to judgment. There is also currently no actionable tort for invasions of privacy. But just as threat actors are entrepreneurial and looking for opportunities, so too are plaintiff law firms.
According to Herbert Smith Freehills’ Partner and Global Co-Head of Class Actions Jason Betts, listed organisations are particularly vulnerable. "When a listed company announces it has been impacted by a data breach, if there is a market reaction, the drop in their share price puts them at risk of a shareholder class action," he says. "This type of claim is in addition to the risk of potential consumer data class actions or representative claims filed with the OAIC.”
The boundaries being tested by plaintiff firms are by no means static. For example, in June 2024, the ASX updated its Listing Rule Guidance Note 8 to include an example of managing continuous disclosure obligations during a fast-moving data breach. APRA has also emphasised its “heightened supervisory focus on cyber resilience, ensuring that all entities meet the requirements"5. Anticipated reforms to the Privacy Act are expected to introduce a direct right of action for individuals, paving the way for class action claims for breaches of privacy. The key issue will become proving loss in quantifiable dollar terms. According to Betts, “once you have a legislated right to privacy that, if breached, leads to a remedy, causation will be an easier element to prove than it is now. Suddenly you have a clear head of loss to sue under, which can lead to damages".
Christine Wong has advised on OAIC representative privacy actions and investigations. She agrees with Betts that the change is significant, given that “recovery for breaches of privacy is broader than for many other potential causes of action" such that "individuals can recover non-economic losses such as anxiety or embarrassment.” Wong emphasises that potential regulatory action, with significant associated civil penalties and ongoing compliance burdens from enforceable undertakings may also be material issues for organisations, alongside class action risks.
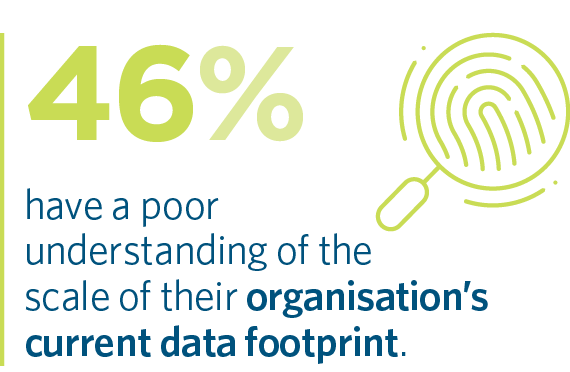
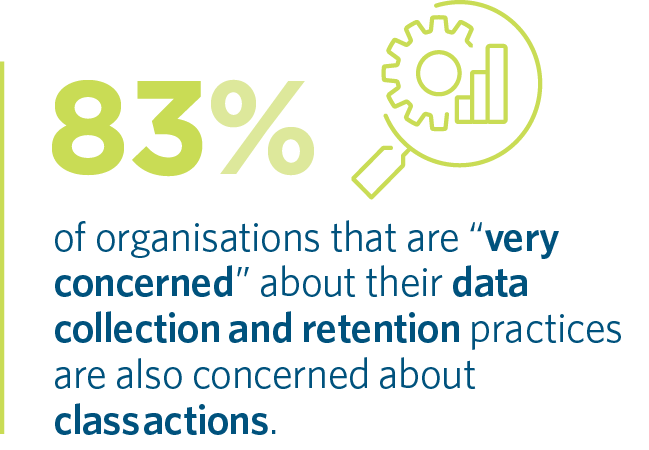
While class action plaintiff law firms have been testing the strength of the data security obligations of impacted organisations, in time this may evolve into an examination of whether the data needed to be collected in the first place. 46% of respondents say their organisation has a poor understanding of their organisation’s data footprint, and that this is a key barrier to improving data collection and retention practices. However, according to Betts, the mere act of probing data storage systems and practices may carry an obligation to resolve any issues identified as part of that exercise. Otherwise, organisations may leave themselves vulnerable to the discovery of documents highlighting a failure to take action. In this context, it is perhaps unsurprising that 83% of organisations who are 'very concerned' about their data collection practices are also concerned about class actions.
Class action risk is being used by threat actors themselves to increase pressure on their targets to pay ransoms. We have seen cases of threat actors warning corporate victims they should expect to lose material amounts in the courts if they decline to co-operate. We have also seen threat actors notify regulators of a breach, again to put pressure on the corporate victim. These are compounded by the escalating cost and complexity of navigating regulatory investigations and related litigation including class actions.

Jason Betts
Partner and Global Co-Head of Class Actions
Data management in the spotlightWhen an attack occurs, organisations have an immediate challenge to identify and interrogate compromised data. Getting a handle on their data footprint and the extent of any exposure is vital. This is so they can meet their regulatory obligations to notify stakeholders expeditiously, then focus on managing the regulatory, financial and reputational fallout. |
|
|
Emily Coghlan, Director, Legal & Legal Technology, Digital Legal Delivery, leads a team at Herbert Smith Freehills that helps organisations identify compromised datasets, and triage and interrogate them quickly. The team can isolate particular sensitive types of data – for example, data containing personal information – using the latest technology tools, and then analyse it. This informs advice regarding the potential impact of the breach, and subsequent obligations such as notifying impacted individuals. “Over the last 12 months, we’ve had to review significant datasets where data has been exfiltrated from businesses and either dumped on the dark web or this has been threatened,” Coghlan says. “The challenge of understanding your data footprint and being able to isolate and extract data really comes into play during a cyber incident where time is of the essence.” If gigabytes or terabytes of data have been compromised, the task of assessing the loss could involve sifting through millions of documents to extract potential personal information. AI tools that leverage pre-trained models are helping to scan data more efficiently and cull the documents that require review. “The technology is coming along quickly. These tools didn’t exist a few years ago and they will get better. Machine learning, large language models and generative AI will help to extract personal information in these massive datasets much more quickly,” Coghlan says. |
It is not possible to protect something you don’t know you have.Andrew Penn, Chair of The Federal Government’s Expert Advisory Panel On Cyber Security Strategy
|
Emily Coghlan
Director, Digital Legal Delivery

The contents of this publication are for reference purposes only and may not be current as at the date of accessing this publication. They do not constitute legal advice and should not be relied upon as such. Specific legal advice about your specific circumstances should always be sought separately before taking any action based on this publication.
© Herbert Smith Freehills 2025
We’ll send you the latest insights and briefings tailored to your needs