Global Bank Review 2024
Adaptation: Change is the only constant
Two years ago, we flagged the transformational opportunities and the threats that quantum computing could bring for the financial sector in our Outlook. Since then, there have been more scientific breakthroughs and investment in quantum technology has increased exponentially. Improvements have led to error reduction and provided the improved stability to enable quantum computing to work at scale.
Alongside operational progress, many countries have released national quantum strategies, including Australia, Canada, China, Denmark, France, Germany, Japan, India, Russia, South Korea, the Netherlands, the UK and the US, and the EU has published its European Declaration on Quantum Technologies. And many financial services firms have established quantum teams to work on potential use cases such as portfolio optimisation, derivatives pricing, simulation, and machine learning. Service providers to the industry are also working on quantum.
Quantum utility is no longer considered a matter of 'if', but of 'when'. McKinsey estimates that there will be between 2000 and 5000 operational quantum computers in 2030. IBM's current roadmap envisages that beyond 2033, the full power of quantum computing will be unlocked. The high-security government sector in Germany is one of many national bodies working to a hypothesis (expressly not a prediction) that cryptographically-relevant quantum computers will be available by the early 2030s. The US National Institute of Standards and Technology (NIST) already has timetables for moving government agencies off current types of encryption onto what they hope will be quantum-resistant encryption by 2035 and the Australian Signals Directorate set an even tighter 2030 cutoff for use of current encryption in High Assurance Cryptographic Equipment.
Ensuring the security of dataResearch is focused on strategies to ensure the security of data to potential quantum-enabled hacking, potential approaches include:
It is generally accepted that PQC should be in combination with current safeguards, eg, the use of pre-shared keys. What is clear is that firms will need to become 'crypto agile' – able to adapt cryptographic solutions or algorithms quickly and efficiently in response to developments in cryptoanalysis, emerging threats, technological advances, and/or vulnerabilities. |
Nicole Sung
Solicitor, Sydney
Three factors affect how long a firm has to transition its systems to use new quantum-safe cryptography1:
Mosca's Theorem
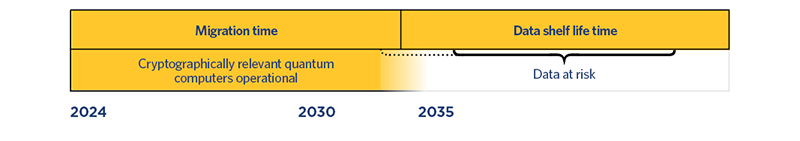
As noted, the current working hypothesis for the development of cryptographically relevant quantum computers is just under 10 years – the early 2030s. While the estimated migration time will vary by firm based on the scale, nature, and complexity of systems, this will be a long-term project – past cryptographic migrations have taken over a decade. Firms need to move now to protect data, not least as firm's existing encrypted data is at risk of being harvested today ready for exploitation when quantum computers become operational.
Financial services regulators have published relatively little in terms of new requirements or granular guidance for firm on managing emerging quantum cyber risks. However, central banks have been seeking to address their own risks. In June 2023, the Bank of International Settlements Innovation Hub, in partnership with the Banque de France (BdF) and the Deutsche Bundesbank published its report on 'Project Leap - Quantum-proofing the financial system'. The initial phase involved the successful implementation of a quantum-safe environment at the network level, building a secure channel of communication to send data as well as payment messages through a post-quantum VPN tunnel. BdF and the Monetary Authority of Singapore (MAS) also plan to extend their joint project to extend PQC to critical financial transactions, particularly cross-border transactions on payment networks.
Globally-agreed supervisory standards for quantum computing in the financial services sector might be a logical next step. In January 2024, the World Economic Forum and the UK's Financial Conduct Authority white paper on 'Quantum Security for the Financial Sector: Informing Global Regulatory Approaches' presented four guiding principles and a roadmap to inform global regulatory and industry approaches. These are high-level, seeking to encourage the reuse and repurposing of existing regulatory frameworks and industry practices, establish a standardised approach, increase transparency through the exchange of information on strategies, best practices and approaches, and foster global thinking to avoid the regulatory fragmentation across different markets. As many financial services regulators adhere to a 'technology neutral' principle, we expect that they will look to apply existing regulatory requirements; operational risk and resilience rules are clearly relevant, but governance (including individual accountability regimes) and other rules will also figure.

Karen Anderson
Partner, London
There is some sector neutral guidance, including the Canadian National Quantum Readiness Best Practices and Guidelines (updated in June 2023).
These set out a range of recommended actions together with suggestions on how to organise these into a quantum-readiness program, using a multi-year and multi-phase timeline involving:
Additional materials cover the use of standardised hybrid cryptography to mitigate some of the risks of migrating to PQC, notes on a systematic approach to thinking about how and where to start migrating quantum-vulnerable IT systems to make use of quantum-safe cryptography by leveraging Cryptographic-Agility; and PQC Roadmap Questions to support system owners and operators in asking when and how their technology providers will introduce PQC capabilities into their products and services.
In August 2023, the Australian Signals Directorate updated its publication 'Protect - Planning for Post-Quantum Cryptography' and in September 2024, updated its guidelines for large organisations and infrastructure (not just financial services firms), also setting down a range of similar preparatory steps. Likewise in December 2023, the Netherlands National Communications Security Agency, the Applied Cryptography and Quantum Algorithms and the Cryptology Group published their PQC Migration Handbook with guidance on the determination of risk, the planning of migration strategies and their execution.
In February 2024, MAS issued a short advisory to all financial institutions on the cybersecurity risks associated with quantum technology, with some recommendations for those institutions to safeguard themselves against the identified threats, including carrying out proof-of-concept trials with quantum security solutions.
In Australia, the Australian Prudential Regulation Authority (APRA) recognises the transformative influence of the quantum computing evolution on the banking sector in its 2024-25 Corporate Plan.2 Prudential Standard CPS 230 (commencing 1 July 2025) establishes minimum standards for APRA-regulated entities to manage operational risk – although CPS 230 does not specifically address quantum computing risks, they would fall under the umbrella of ‘operational risk’.3 The Australian Securities & Investments Commission (ASIC) has also signalled that its forthcoming actions include the development of supervisory approaches for emerging operational risks, including quantum computing.
Charles McGrath
Senior Associate, London

In August 2024, NIST issued its finalised principal4 set of encryption tools (algorithms) designed to withstand the attack of a quantum computer, which are ready to use. These post-quantum encryption standards are designed for:
NIST says full integration will take time and urges system administrators to start integrating these standards into their systems immediately.
In Europe, working groups at the European Telecommunications Standards Institute (ETSI), a standards organisation, are exploring how the NIST standards will fit into existing protocols, applications, and public-key infrastructures.
In October 2024, the G7 Cyber Expert Group, chaired by the US Department of the Treasury and the Bank of England, issued a public statement referring to the release of the NIST Standards. That statement echoes others in strongly encouraging financial authorities and institutions to take steps now to build resilience, including:
Shortly thereafter, the Financial Services - Information Sharing and Analysis Center (FS-ISAC), a member-driven, not-for-profit organisation that advances cybersecurity and resilience in the global financial system, published its white paper 'Preparing for a post quantum world by managing cryptographic risk'. The paper aims to help financial services institutions understand the challenges, elements, and processes of building cryptographic agility in the face of emerging threat vectors like quantum computing. FS-ISAC stresses the need for the financial services sector to boost its capacity for implementing, updating, replacing, and adapting software, hardware, and infrastructure cryptography, such that no significant architectural changes are incurred and without disruption to running systems.
Although engagement is growing, the threat that quantum computers will pose is still widely underestimated.5
So far, financial services regulators have not regulated to address quantum computing risks specifically. Firms may draw some comfort about the general level of recognition of the issues which is attested by the various recent publications, but a harmonised approach is needed to avoid regulatory fragmentation across different markets.
The first post-quantum cryptographic standards are available and there is a body of good practice guidance to support firms in their migration plans. Based on the working hypothesis that cryptographically-relevant quantum computing will emerge in the early 2030s, it is imperative that financial services firms focus on the work needed for migration to quantum-safe cryptography now.
1 Michele Mosca, 2015 'Cybersecurity in a Quantum World: will we be ready?'
2 See under ‘Technology and Innovation’: https://www.apra.gov.au/apra-corporate-plan-2024-25
3 APRA defines ‘operational risk’ as the potential for financial loss or material disruption as a result of inadequate or failed internal processes or systems, the actions of people or external drivers and events.
4 NIST is continuing to evaluate two other sets of algorithms that may serve as backup standards (one focused on general encryption and the other on digital signatures) but says there is no need to wait for future standards.
5 Informal surveys of attendees at our events also suggest many may not yet have engaged fully with the issues.
The contents of this publication are for reference purposes only and may not be current as at the date of accessing this publication. They do not constitute legal advice and should not be relied upon as such. Specific legal advice about your specific circumstances should always be sought separately before taking any action based on this publication.
© Herbert Smith Freehills 2025
We’ll send you the latest insights and briefings tailored to your needs